What is rule-based detection when compared to statistical detection?
A.
proof of a user's identity
B.
proof of a user's action
C.
likelihood of user's action
D.
Dfalsification of a user's identity
proof of a user's action
Which two elements are used for profiling a network? (Choose two.)
A.
session duration
B.
total throughput
C.
running processes
D.
listening ports
E.
EOS fingerprint
listening ports
EOS fingerprint
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
A.
resource exhaustion
B.
tunneling
C.
traffic fragmentation
D.
timing attack
resource exhaustion
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
A.
forgery attack
B.
plaintext-only attack
C.
ciphertext-only attack
D.
meet-in-the-middle attack
ciphertext-only attack
What does cyber attribution identify in an investigation?
A.
exploit of an attack
B.
threat actors of an attack
C.
vulnerabilities exploited
D.
cause of an attack
threat actors of an attack
Which two elements of the incident response process are stated in NIST Special
Publication 800-61 r2? (Choose two.)
A.
detection and analysis
B.
post-incident activity
C.
vulnerability management
D.
risk assessment
detection and analysis
post-incident activity
Reference: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A.
best evidence
B.
prima facie evidence
C.
indirect evidence
D.
physical evidence
indirect evidence
the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
A.
best evidence
B.
prima facie evidence
C.
indirect evidence
D.
physical evidence
indirect evidence
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor. Which type of evidence is this?
A.
best evidence
B.
prima facie evidence
C.
indirect evidence
D.
Dphysical evidence
indirect evidence
Refer to the exhibit.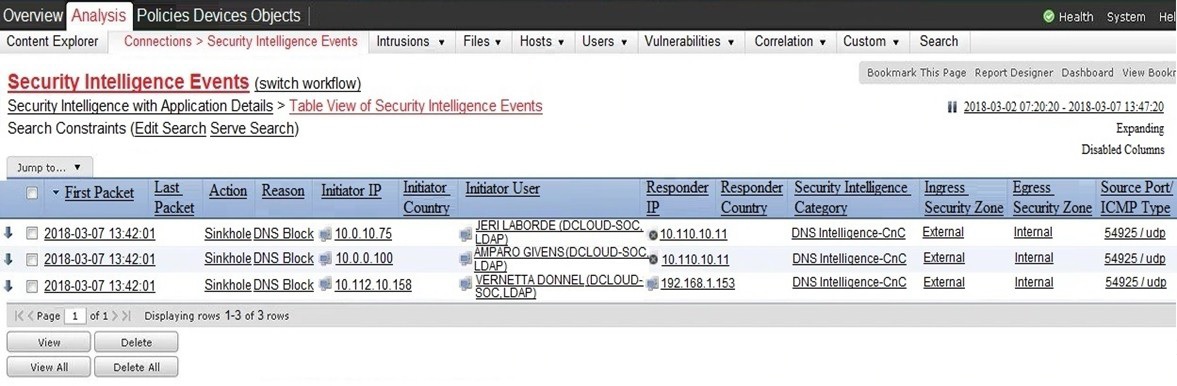
Which two elements in the table are parts of the 5-tuple? (Choose two.)
A.
A. First Packet
B.
Initiator User
C.
Ingress Security Zone
D.
Source Port
E.
Initiator IP
Source Port
Initiator IP
| Page 1 out of 19 Pages |